
Could your phone system be a security risk waiting to happen?
When a burglar wants to break into a house, they generally conduct their own risk assessment before doing so:
![]()
Is there anyone at home?
![]()
How difficult will it be to open locked doors or windows?
![]()
Is there an alarm system, and if yes, how easily can it be disabled?
If the expected value of the items they intend to steal from the house outweighs the risks of breaking in, that’s when they will make their decision. When hacking a business phone system, the principles are similar, but the scale is different.
 With the global VoIP market predicted to reach $93.2 billion by 2024, phone system hacking and exploitation is fast becoming a lucrative undertaking for suitably skilled cyber criminals. With the value of these ill-gotten gains rising exponentially year-on-year, it is essential for everyone in the industry including the carriers, service providers, system integrators, IT administrators/users and of course the hardware and software vendors and manufacturers themselves to prioritize and improve network security.
With the global VoIP market predicted to reach $93.2 billion by 2024, phone system hacking and exploitation is fast becoming a lucrative undertaking for suitably skilled cyber criminals. With the value of these ill-gotten gains rising exponentially year-on-year, it is essential for everyone in the industry including the carriers, service providers, system integrators, IT administrators/users and of course the hardware and software vendors and manufacturers themselves to prioritize and improve network security.
Not only the increase in IP telephony global market share is providing an attractive target for hackers, but also changing business behavior. And with a faster-paced switch to remote working than previously predicted, the proliferation of BYOD (bring your own device) amid an increase in carriers switching to all-IP solutions, not only is the market expanding but also rapidly changing, and where there is change there are uncertainties and unpredictable developments which provide fertile ground for those criminally inclined to exploit any opportunities.
But how do they do it?
What are the most common methods for the criminally inclined and technically au fait hacker? How about a break in? In order to gain access to a telephony system, hackers need the password of the device they are targeting. In order to gain this password and successfully compromise an IP-PBX system, hackers will identify an IP extension on the network, and then bombard that device with different passwords in the hope that one of them will be right. Although this sounds like a long shot, many users don’t change their passwords from the default setting. Also, hackers can send thousands of passwords to an extension in just a couple of minutes. In many cases, it doesn’t take long for the hackers to guess the correct password and logon to the IP-PBX system. Or alternatively, they may identify weaknesses in a system so that they can bypass or overwrite password requirements or utilize phishing methods by, for example, pretending to be IT admin to obtain passwords.

Sadly, the number of threats to networks is on the increase and a cursory search reveals an ominous list of malign attacks including “Brute Force”, “Man in the Middle”, DDoS (Distributed Denial of Service) and “Spoofing”, all of which pose a serious threat to unsecured communications.
Once a hacker has access to the system, there are many ways in which they can disrupt the IP telephony network and potentially cause the business to lose large sums of money. One of the most common attacks, and indeed one of the most damaging, is when professional criminals attach an entire call center to the compromised network connection, routing thousands of calls over the one connection in a short period of time. Depending on how the IP-PBX routes its calls, and how regularly the company receives its bills, this activity can continue for months before being discovered, running up an astronomical telephone bill.
While this is the primary way for hackers and fraudsters to take advantage of a poorly-protected system, weak passwords and a lack of encryption in an IP-PBX infrastructure can leave the doors wide open to other types of malicious activity. For example, as a result of the computerized nature of IP telephony, it is much simpler than with fixed-line telephones to secretly record internal calls. Rather than having to install a physical device, calls can simply be recorded using the right software. Often, this kind of threat comes from an employee inside the organization, making it difficult to protect against. If a company is using an unencrypted VoIP protocol, then there is no barrier in place to stop calls from being recorded. Even if the threat doesn’t come from an employee, or outside groups with an interest in recording a company’s telephone conversations, a Trojan could be used to install the recording tool. And things could get even worse if the phone is used to get into the company’s network – entering the entire server structure, like a burglar accessing a house via the cellar.
How to secure your calls with Snom
Think of it like this: We provide a reliable lock for your back door, front door, hatch to the cellar and to all the rooms in your house. We also supply the keys to these locks, but it is still up to the owner to ensure that the doors are actually locked.
“Every day of the year Snom is running automated security test protocols with real Snom phones in real PBX environments.” Snom’s Jan Boguslawski describes how Snom keeps track of potential new threats: “We have rooms with banks of Snom phones being tested in a sped-up but true-to-life environment. Basically, the ATF (Automatic Test Framework) we run at Snom continuously tests our software. This means we are eliminating security issues and updating our software before a problem has even been detected by our customers. In other words, we are proactively identifying and fixing issues, rather than waiting for customers to come banging on the door of our support team screaming for help. I believe as an IP phone manufacturer we are quite unique in that respect.”
In addition to running a non-stop ATF security and software check, Snom provides users with a comprehensive overview for implementing security and privacy measures on its service hub, service.snom.com. Topics covered include Port Authentication via 802.1x, Dynamic Blacklist Check. DECT encryption, TLS support and Snom devices in a VPN. A number of useful “how-to” articles on securing a Snom phone in four really easy steps via the phone’s web interface:
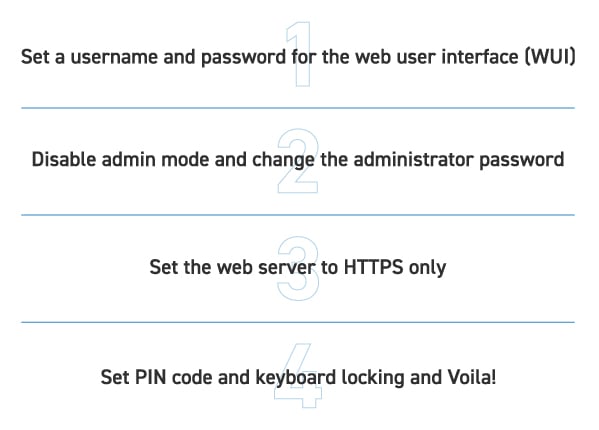
Other areas covered include auto-provisioning a VPN on a desk phone, preventing unauthorized or unqualified access to the phone interface, and much more besides to provide users and admins with a comprehensive step-by-step guide to ensuring that Snom phones are secure in any telephony environment.
In the end, Snom as a manufacturer and supplier, can make customers of its products and software aware of the necessity of an effective password policy via pop-up warnings and reminders. Snom can also work with customers who implement network encryption, but it is ultimately the responsibility of the customer to ensure that these measures are implemented.
Who else needs to take responsibility?
The telecommunications security chain is comprised of several equally crucial links. One of these key links is, of course, the IT administrator in a company. It is an inescapable reality that the IT administrator must take some responsibility for protecting the security of their company’s network by implementing an effective password policy and informing staff and colleagues of their requirements. Prioritizing seamless communication over security is something that, under a given set of circumstances, can occur. This can be compared to leaving the keys to your house under a flowerpot near to your front door so that someone else can enter.
The risks have to be carefully weighed, and in the end, this should never be considered as an ongoing solution. At the end of the day, security is one of those things that only gets noticed when something goes wrong. A thankless task for those who must ensure that security systems are maintained. How often do office staff thank the building management for a year free of break-ins? It is easy to forget how important security really is when it is working well. Ongoing security requires the vigilance and awareness of several key links in the chain that locks the door.
How much?!? Network security means financial security.
What is the cost of a phone system being hacked? Well, in 2016 it was calculated at $38.1 billion (globally), of which $3.53 billion was via IP-PBX.
This figure, year-on-year has been growing exponentially. Just imagine the following: A small company of say 25 staff suddenly gets billed a six-figure sum for calls made during just one week. On closer inspection, the calls are revealed to have been made to premium-cost numbers in countries where the money quickly vanishes into a shadowy, untraceable financial system. In the worst case, these costs can instantly bankrupt a business. The best case? A rude awakening to the importance of network security. Ensuring that company employees are regularly trained in matters of IT security is something that should be an ongoing process and not a one-off. Sales teams, customer support, switchboard – all of these essential functions are potential weak links in the security chain.
In recent times, a whole host of security challenges have arisen with more people working remotely or from home and using their own devices in a company network (BYOD). The danger to businesses has multiplied immeasurably in the space of just a few months. To neglect these weak new links in the security chain would be extremely perilous.
Looking into the crystal ball…
Imagine we are in the year 2025. There has been a catalogue of major changes to technology and behavior. People across the entire world have a multitude of tailored communications solutions designed to meet all of their personal and business requirements at their fingertips. To get to this point however, many businesses, across all industries and scales, have been lost. Their legacy is a lesson in security: take responsibility, maintain ongoing reviews, leave no stone unturned and shine a torch on every shadow.
 This over-simplified statement is of no help to those responsible for their business’ security today, but what might help is to understand that we at Snom, and our partners, work to the highest standards of development and innovation. As a fundamental basis of IP telephony and in recognition of our responsibilities, security is an area to which we dedicate a great deal of our resources.
This over-simplified statement is of no help to those responsible for their business’ security today, but what might help is to understand that we at Snom, and our partners, work to the highest standards of development and innovation. As a fundamental basis of IP telephony and in recognition of our responsibilities, security is an area to which we dedicate a great deal of our resources.
High profile and/or expensive hacking cases, the proliferation of “SPIT” (Spam over Internet Telephony) and other unsolicited calls will continue to make the headlines, but as the old saying goes, “forearmed is forewarned”: Only a combination of manufacturers, interop partners, integrators, resellers and end users can contribute to an increase in security awareness and best practices. Snom has, is, and will continue to play its part in this team effort.

